In this tutorial you will learn how to output the hashes with bloodhound-python and display the data as a schema in bloodhound.
Prerequisites
- Valid credentials on a machine linked to the domain.
- neo4j, bloodhound and bloodhound-python must be installed on your attacking machine.
What is Bloodhound
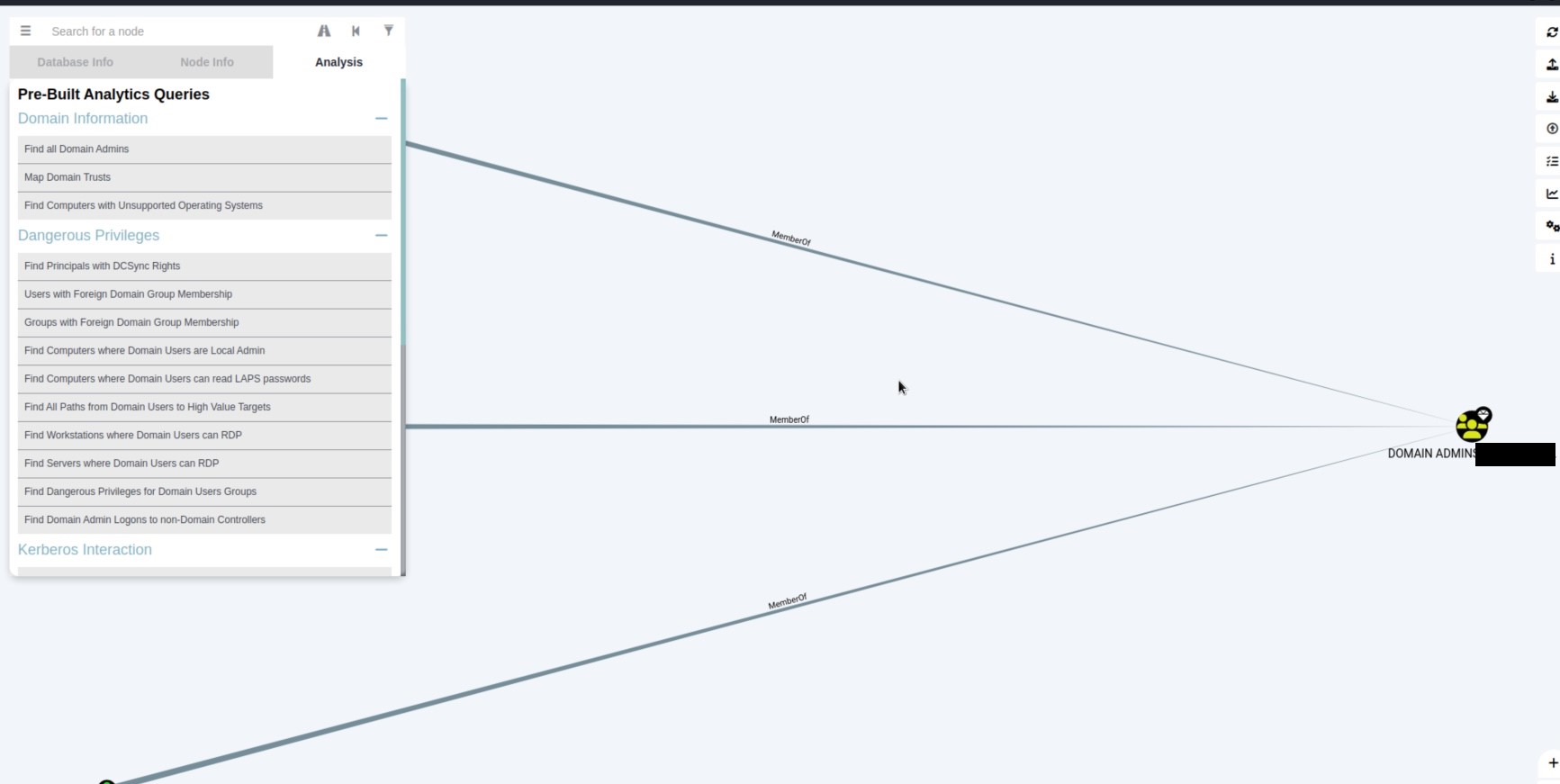
BloodHound is an Active Directory (AD) reconnaissance tool that can reveal hidden relationships and identify attack paths within an AD environment.
Installation:
- You can install bloodhound with this command:
apt install bloodhound
How to make it work
- Extract the json used to populate bloodhound with this command
bloodhound-python -u USER -p 'PASSWORD' -ns IP -d DOMAIN -c all - Start Neo4j with this command. If this is the first time you have used the neo4j service, you will have to create identification information when starting the service
sudo neo4j console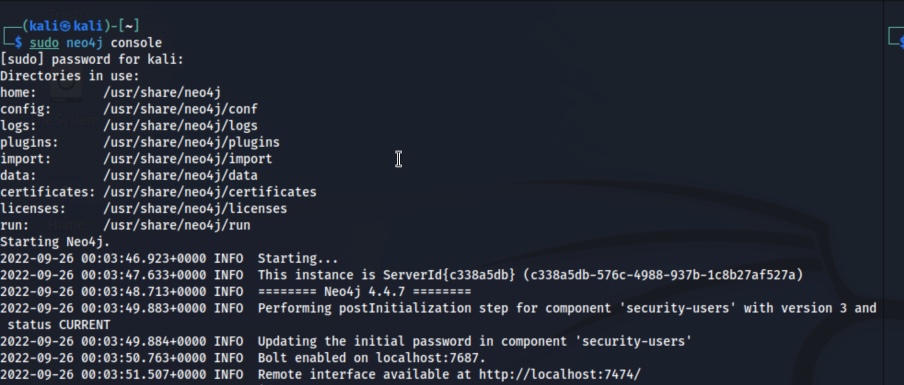
- Start bloodhound with this command :
bloodhound
-
Connect to bloodhound with the same credentials you created for neo4j
- With the upload function you can upload the json file you extracted with bloodhound-python

** You are now ready to visualize the relations of the active directory **