Basic SSL Pinning Bypass
This tutorial will guide you through setting up Burp Suite, configuring certificates on an Android emulator, and using Frida for ssl pinning bypass.
Prerequisites
- Burp Suite installed on your machine.
- Android emulator set up and running.
- OpenSSL installed.
- Frida installed.
1. Download the Burp Suite Certificate
First, you need to download the Burp Suite certificate that will be used to intercept traffic on your Android emulator.
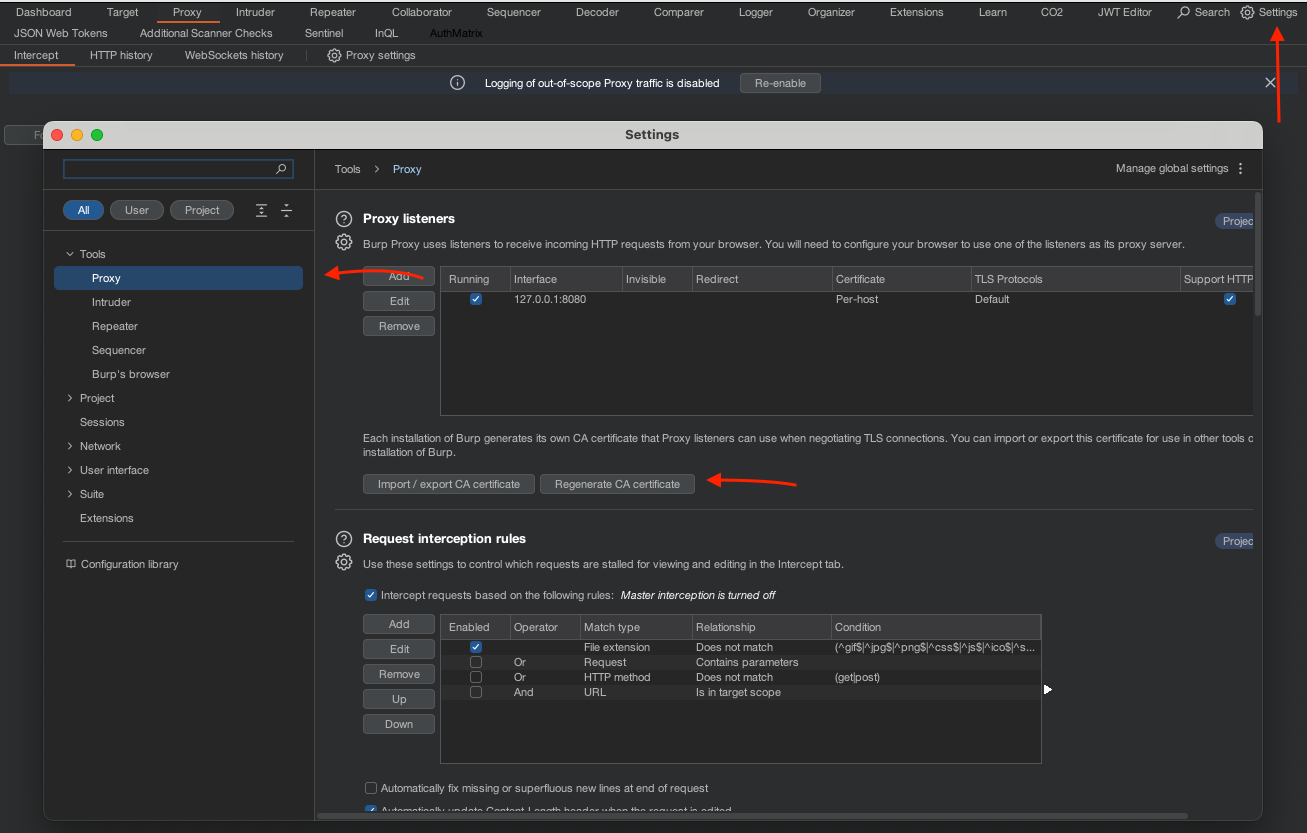
- Open Burp Suite.
- Go to
Proxy>Options>Import / export CA certificate. - Export the certificate in DER format.
2. Convert the DER Certificate to CRT Format
The certificate downloaded from Burp Suite is in DER format. Convert it to CRT format using the following command:
openssl x509 -inform der -in cert -out cert-der.crt
This command transforms the DER certificate into a CRT certificate, which can be installed on the Android emulator.
3. Push the Certificate to the Emulator
Next, push the converted CRT certificate to the appropriate location on the Android emulator. Use the following command:
adb push cert-der.crt /data/local/tmp/cert-der.crt
4. Transfer the APK and CRT Certificate to the Emulator
Transfer the APK file of the mobile app you want to analyze and the CRT certificate to the emulator:
- Push the APK file to the emulator.
- Push the CRT certificate to the same location on the emulator.
5. Configure the Proxy and Install the Certificate
Configure the Android emulator to route traffic through Burp Suite by setting up the proxy:
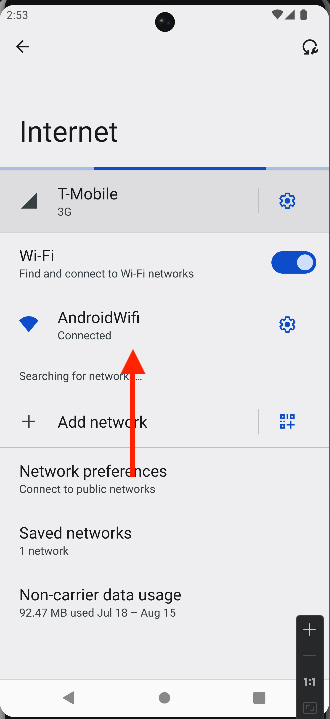
- Go to
Settings>Network & Internet>Wi-Fi. - Press on your connected network, then select
Modify Network.
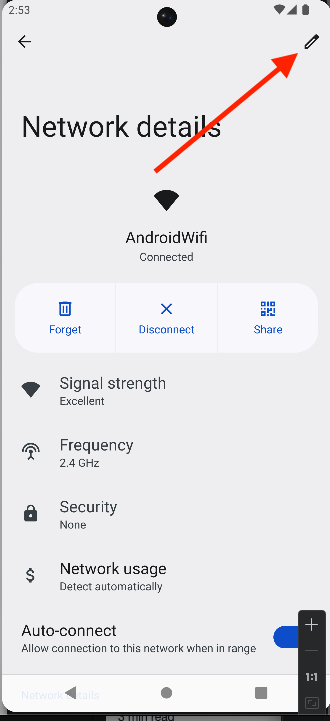
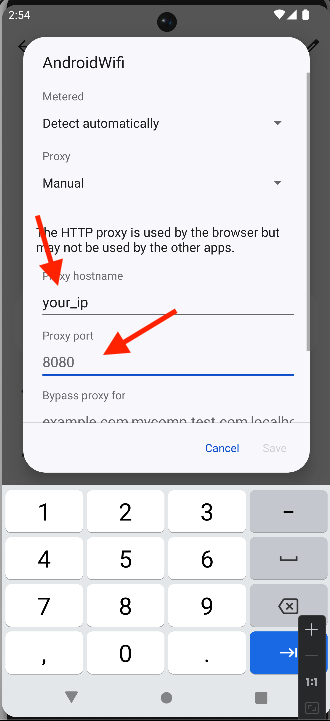
- Set the
ProxytoManualand enter your machine’s IP address and the port used by Burp Suite (default is8080).
Install the CRT certificate:
- Navigate to the location where you pushed the certificate on the emulator.
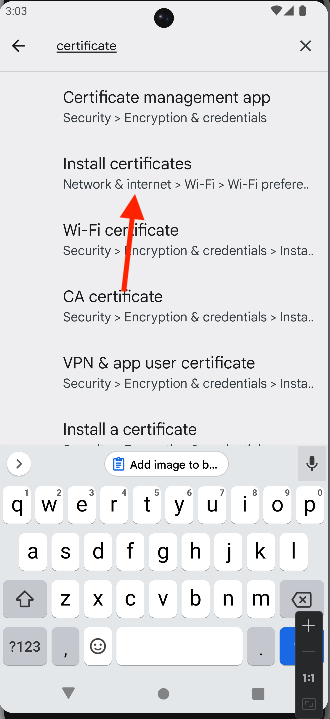
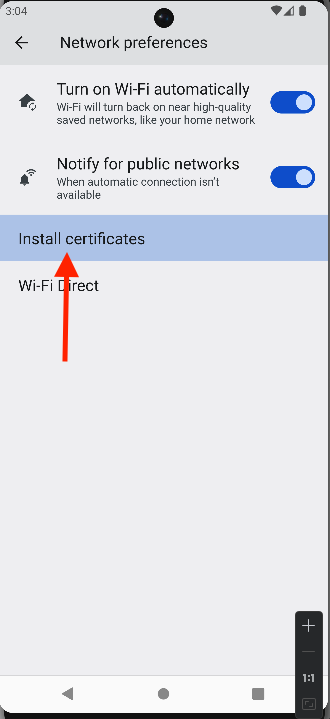
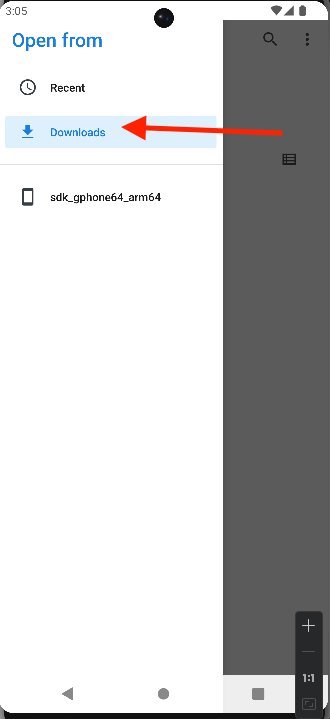
- Open the CRT file and install it as a trusted certificate.
6. Push the Frida Server to the Emulator
To analyze the mobile app, push the Frida server to the emulator using the following command:
adb push frida-server-16.1.11-android-arm64 /data/local/tmp/frida-new-server
7. Start the Shell on the Emulator
Access the shell on the emulator to run the Frida server:
adb shell
su
8. Make the Frida Server Executable and Run It
Once you’re in the shell, make the Frida server executable and then execute it:
cd /data/local/tmp
chmod +x frida-new-server
./frida-new-server
9. Execute the Frida Script
Now that the Frida server is running, execute the Frida script on the mobile app using the following command:
frida -U -f <PACKAGE_NAME> -l fridascript.js
Replace <PACKAGE_NAME> with the actual package name of the mobile app you’re analyzing.
Conclusion
This setup allows you to perform security testing on Android applications using Burp Suite and Frida.
